Security
Critical aspect of tech, safeguarding systems, networks, and data from unauthorized access, attacks, and breaches, ensuring confidentiality, integrity, and availability for users and businesses.
Created on
Oct 15, 2022
5
Posts
5
Followers
Why Char[] is Preferred over String for Passwords
In security-sensitive applications, storing passwords securely is crucial to prevent unauthorized access. One common practice is to use char[] arrays...
Encrypting HTTPS Headers
HTTPS (Hypertext Transfer Protocol Secure) is a secure version of HTTP that encrypts data to protect it from eavesdropping and tampering.
Understandin...
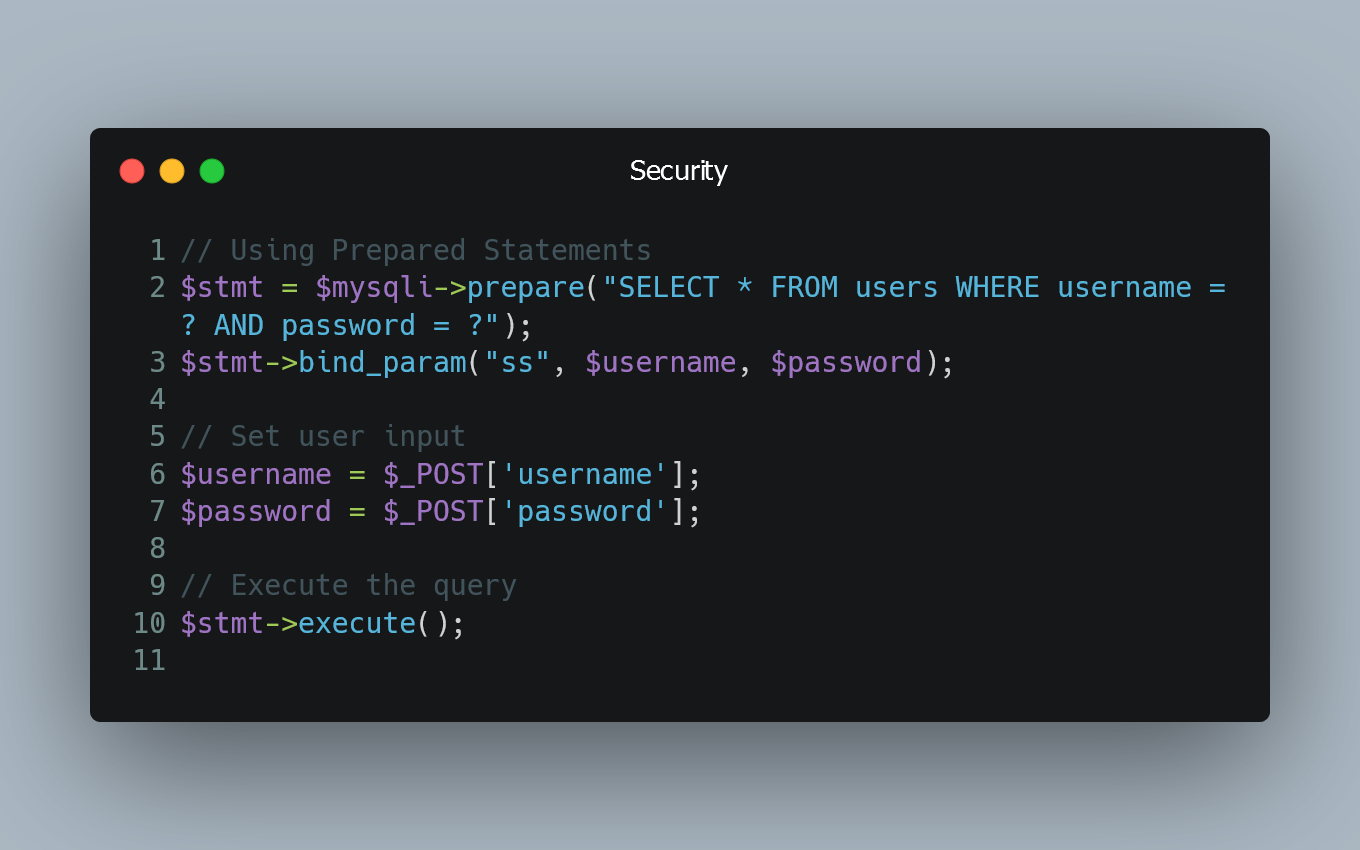
Preventing SQL Injection in PHP
SQL injection is a serious security vulnerability that occurs when untrusted data is inserted into a SQL query, allowing attackers to manipulate the q...
Creating a .pfx File from Certificate and Private Key
A .pfx file (Personal Information Exchange) is a container format that holds both the public certificate and its associated private key. It is commonl...
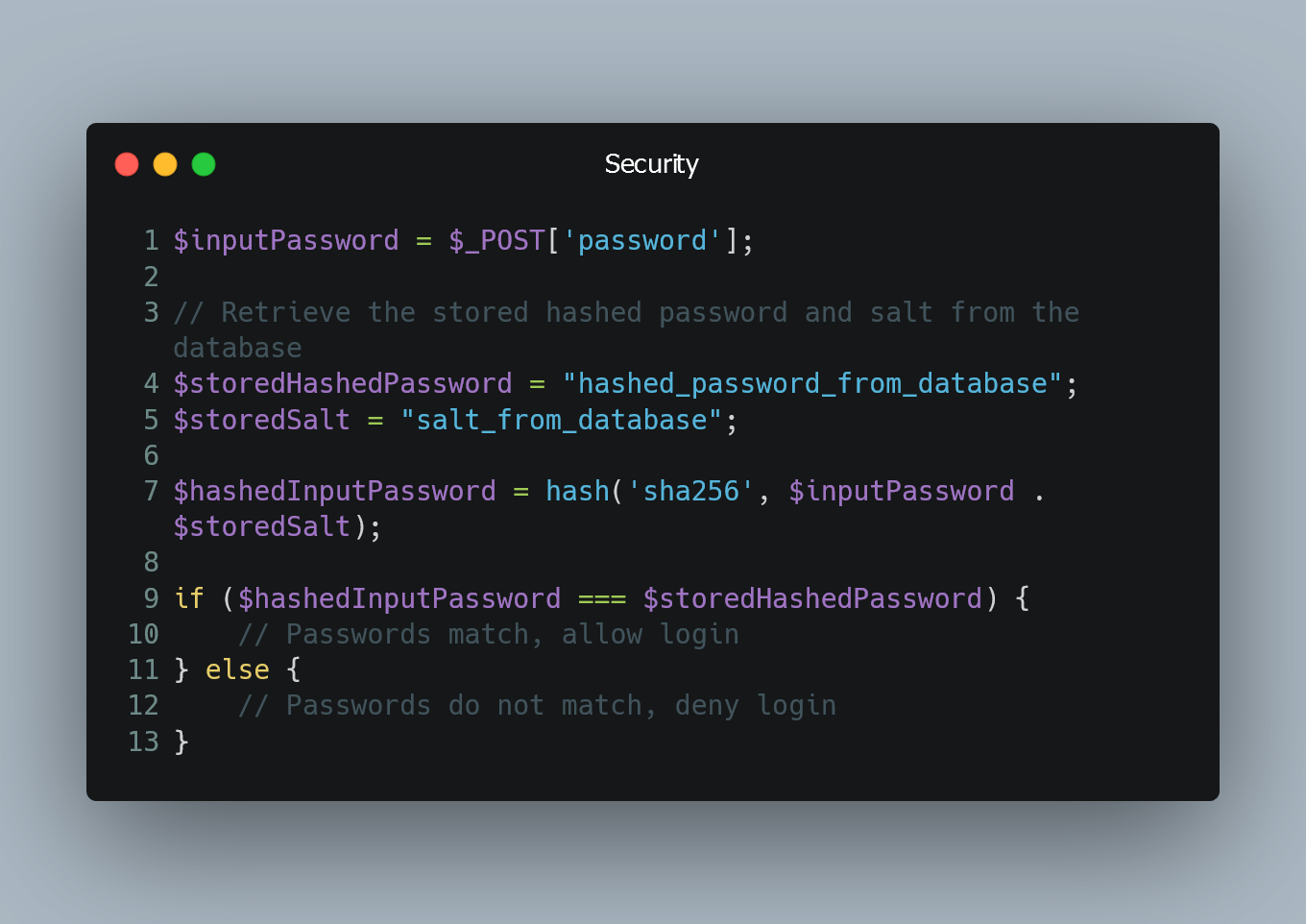
Secure Hash and Salt for PHP Passwords
Securing user passwords is critical to protect user accounts from unauthorized access and data breaches. In PHP, using a strong hash function and salt...